Launch of C|EH v13 Ai worldwide: Greetings from (C|EH) Ai
Even though malevolent actors are using AI more frequently to carry out unprecedented cyberattacks, security experts may now employ AI…
How to Become a Cybersecurity Engineer
Find out how to become a cybersecurity engineer by reading about the required education, certifications, and abilities, among other things.Entering…
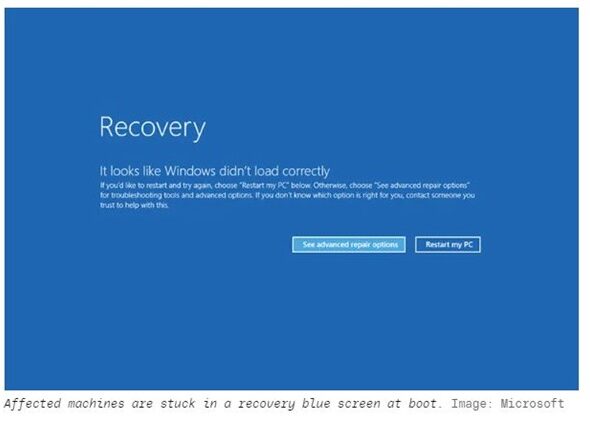
What happened during the CrowdStrike Windows Outage and What to Do Nexts ??
What happened during the CrowdStrike Windows Outage and What to Do Nexts ?? Windows PCs running the CrowdStrike upgrade are…
Comparison between OSCP and CPENT
As the world’s reliance on technology grows, enterprises must prioritize cybersecurity to secure their data and networks from cyber threats.…
Unlock Your Ethical Hacking Potential with CEH Training in Mumbai
CEH Training in Mumbai provided by Macksofy Technologies serves as your pathway to mastering hacking skills with a team of over…
New High-Severity Vulnerabilities Discovered in Cisco IOx and F5 BIG-IP Products
F5 has warned of a high-severity flaw impacting BIG-IP appliances that could lead to denial-of-service (DoS) or arbitrary code execution.…
Hack The Box Writeup – Laboratory
Greetings from Macksofy Technologies. Below is the detailed walkthrough of the Laboratory machine which got retired from HackTheBoxThe IP of this box is 10.10.10.216Port…
HackTheBox Writeup – Time
Greetings from Macksofy Technologies. Below is the detailed walkthrough of the Time machine which got retired from HackTheBox The IP of this box…
HackTheBox Writeup – Luanne
Greetings from Macksofy Technologies. Below is the detailed walkthrough of the Luanne machine which got retired from HackTheBox The IP of this box…
HackTheBox Writeup – Passage
Greetings from Macksofy Technologies. Below is the detailed walkthrough of the Passage machine which got retired from HackTheBox The IP…