Greetings from Macksofy Technologies. Below is the detailed walkthrough of the Luanne machine which got retired from HackTheBox
The IP of this box is 10.10.10.218
Port Scan
Running NMAP full port scan on it , we get
There were 3 Open Ports found, Port 22, 80 and 9001 respectively
Web
Checking the web, it asks for basic authentication
Default random credentials didn’t worked here, so checked robots.txt file and got a disallowed entry as /weather
The directory returns a 404 error, but from the robots file it told us its still harvesting cities
Running Gobuster, I found a directory named /forecast
The directory is an API which is returning a 200 status code and also a message saying that no city is specified and also tells us to use the city parameter to list the available cities
Listing out the cities , I got 13 cities listed as shown
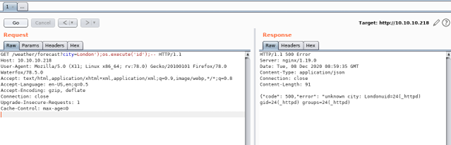
Injecting a single quote in the end of the argument value, it returns a Lua error in the response
Using command execution payload for Lua as shown to print the message hello
Now execution shell command to run the id command using the os.execute functionality
Since command execution was confirmed, I took a reverse shell successfully
Enumerating
the web, I found a .htpasswd file which has the hash for webapi_user
Using
hashcat to crack the hash successfully to iamthebest
Checking locally open ports, it was found Port 3000 and Port 3001 was open
Checking the process running, it can be seen that httpd is running locally on Port 3001
Using curl command to get the contents using the basic authentication locally and found a id_rsa file listed
Getting the contents of the private ssh key using the same way
Connecting to the user r.michaels using the private key successfully
Way To Root
Checking the current user directory, there was a backups folder
Inside the backups directory, was a encrypted zip file which was encrypted using netpgp
Use netpgp tool to decrypt the file and get the zip file
Inside the zip folder there was another .htpasswd hash found
Used hashcat tool to crack the password to littlebear
Used the password to run the sh shell as root and provide the password which I got and it led me to root shell successfully





