Blog
LLM02: 2025 Sensitive Information Disclosure
Exploring AI Vulnerabilities Through the Lens of the OWASP Top 10 – Part 2 LLM02: 2025 Sensitive Information Disclosure(Continued from…
The Ultimate 2025 Guide to Choosing the Best Cyber Security Training Institute
Intro: Why Cybersecurity is Your Golden Ticket in 2025 Macksofy Cyber Security Training Institute isn’t just a classroom—it’s your launchpad to a…
Introduction to the Series: Exploring AI Vulnerabilities Through the Lens of the OWASP Top 10.
Artificial intelligence (AI) has altered industries, streamlined corporate processes, and brought astonishing improvements to our daily lives. However, as AI…
OSCP Training and Certification In Mumbai-UAE
OSCP Training and Certification – PEN 200 With the help of excellent course content produced by Offsec, the well-known powerhouse…
Launch of CEH v13 Ai Course worldwide
Greetingsfrom Ceh v13 Ai Course Even thoughmalevolent actors are using AI more frequently to carry out unprecedentedcyberattacks, security experts may…
How to Become a Cybersecurity Engineer
Find out how to become a cybersecurity engineer by reading about the required education, certifications, and abilities, among other things.Entering…
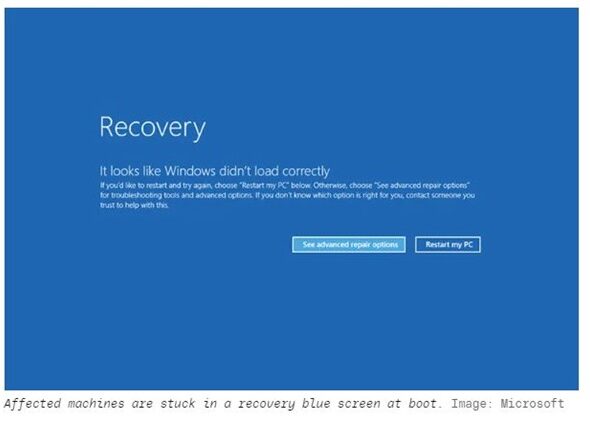
What happened during the CrowdStrike Windows Outage and What to Do Nexts ??
What happened during the CrowdStrike Windows Outage and What to Do Nexts ?? Windows PCs running the CrowdStrike upgrade are…
Comparison between OSCP and CPENT
As the world’s reliance on technology grows, enterprises must prioritize cybersecurity to secure their data and networks from cyber threats.…
Unlock Your Ethical Hacking Potential with CEH Training in Mumbai
CEH Training in Mumbai provided by Macksofy Technologies serves as your pathway to mastering hacking skills with a team of over…
New High-Severity Vulnerabilities Discovered in Cisco IOx and F5 BIG-IP Products
F5 has warned of a high-severity flaw impacting BIG-IP appliances that could lead to denial-of-service (DoS) or arbitrary code execution.…